Bitcoin’s Layer-2 solutions, Liquid Network and Lightning Network, rely on threshold key generation for secure transactions. This method splits private keys into multiple shares, ensuring no single party can compromise your assets. However, their distinct architectures - Liquid’s federated model and Lightning’s decentralized framework - create unique challenges for security audits.
Key takeaways:
- Liquid Network: A federated sidechain with structured governance. Audits focus on functionary operations, Bitcoin peg management, and Confidential Transactions.
- Lightning Network: A decentralized payment system. Audits address node diversity, real-time transaction processing, and routing complexities.
Quick Comparison
| Aspect | Liquid Network | Lightning Network |
|---|---|---|
| Key Management | Centralized functionary model | Decentralized, node-based |
| Transaction Type | Block-based settlements | Real-time micropayments |
| Audit Scope | Functionary operations, peg management | Node/channel operations, routing security |
| Complexity | Controlled, predictable environment | Dynamic, diverse setups |
| Audit Frequency | Scheduled periodic reviews | Continuous monitoring |
Both systems need rigorous audits to maintain security. Liquid benefits from predictable oversight, while Lightning’s real-time nature demands constant vigilance. The article dives deeper into how these systems are audited and the role of tools like BitVault in ensuring secure Bitcoin custody.
Threshold Key Audits in Liquid Network

The Liquid Network functions as a federated sidechain with a structured governance model. This setup enables a system for threshold key audits, where a consortium of trusted functionaries oversees key operations tied to the Bitcoin peg. Auditors play a critical role in verifying the network's cryptography and overall security. Below, we'll dive into Liquid's federated multisignature model and the specific audit challenges it presents.
Federated Multisignature Model
In the Liquid Network, threshold keys essential for Bitcoin peg operations are managed by a group of trusted functionaries. The network uses a threshold signature scheme, allowing a predetermined subset of these functionaries to approve transactions. This design ensures decentralized control while maintaining efficiency. Audits focus on ensuring compliance with cryptographic standards and hardware security measures, such as secure key storage and proper key rotation practices. These elements form the backbone of Liquid's governance and security, but they also introduce unique challenges for auditors.
Liquid-Specific Audit Requirements
Liquid's advanced features, like Confidential Transactions, add an extra layer of complexity to the audit process. Confidential Transactions use cryptographic commitments to obscure transaction amounts, requiring auditors to verify the proper handling of these blinded values and the integrity of the cryptographic proofs. Additionally, the network's asset issuance and recovery functionalities demand meticulous key management checks to ensure no vulnerabilities exist.
Audit Scope and Depth in Liquid
The design of the Liquid Network expands the scope of threshold key audits beyond basic checks. Auditors must also assess multi-asset custody, emergency recovery mechanisms, and cross-chain coordination to ensure the network's security and reliability. Furthermore, timing and performance metrics are scrutinized to confirm that threshold key operations can handle the network's demands without any compromise in security or efficiency.
Threshold Key Audits in Lightning Network

The Lightning Network functions as a decentralized payment protocol, offering a unique audit environment compared to Liquid's federated setup. Its peer-to-peer channel structure and real-time transaction handling introduce distinct challenges for threshold key audits, demanding tailored methods to ensure security across countless independent nodes and payment channels.
Threshold Signatures in Lightning
In the Lightning Network, threshold signatures play a critical role in managing payment channels. Unlike Liquid's centralized functionary model, Lightning delegates threshold key responsibilities to individual node operators, each managing their own channels. Every channel transaction - whether moving funds or closing the channel - requires mutual threshold signatures from the involved parties.
Hash Time-Locked Contracts (HTLCs) further complicate the process. These contracts require multiple signature verifications across routing paths, meaning auditors must confirm that threshold key implementations can handle these cascading signature demands without creating vulnerabilities. Additionally, channel factories and multi-party channels involve multiple participants rather than just two, introducing an extra layer of complexity for audits.
Another challenge lies in Lightning's revocation key mechanism. When channel states are updated, older commitment transactions must be invalidated using threshold signatures. Auditors need to ensure that these revocation keys are securely generated, stored, and accessible at the right time to prevent fraudulent activities. These intricate signature requirements highlight the unique hurdles faced in auditing within a decentralized framework.
Decentralized Audit Environment
Auditing in the Lightning Network is inherently different due to its decentralized nature. With thousands of active nodes, auditors cannot rely on centralized checkpoints or uniform security standards. Instead, they need to develop robust frameworks capable of assessing threshold key security across a wide variety of node implementations and hardware setups.
Auditors must verify that multi-party channel operations and ongoing node communications maintain the integrity of threshold signatures. Lightning's gossip protocol, which relies on cryptographic signatures to exchange network information, adds another layer of complexity. Audits must ensure that threshold key implementations support secure, continuous communication without exposing sensitive key material.
The inclusion of watchtower services - third-party entities that monitor channels for potential fraud - further complicates audits. These services require access to specific threshold key data, and auditors must confirm that such integrations do not compromise the security of the threshold key schemes while still providing effective fraud detection.
With these distributed challenges in mind, the fast-paced nature of Lightning transactions demands an additional layer of scrutiny.
Real-Time Transaction Audit Challenges
Beyond the complexities of decentralization, the Lightning Network's real-time transaction processing introduces its own set of hurdles for threshold key audits. Unlike Liquid's relatively predictable transaction patterns, Lightning’s high-volume micro-payments demand rapid and secure threshold signature validations.
Performance under heavy load is a critical area of focus. Auditors must ensure that threshold key systems maintain security standards during high-speed payment updates. Key generation and signature processes should remain robust, even during peak transaction volumes, without introducing timing vulnerabilities or compromising the randomness of key material.
The routing of Lightning payments adds another layer of difficulty. A single payment may pass through multiple channels, each requiring threshold signature validation. Failed payments trigger rollback procedures involving multiple signature operations, which auditors must evaluate for potential security gaps.
State synchronization is another ongoing challenge. Lightning channels rely on off-chain states that must stay synchronized between parties using threshold signatures. Auditors need to ensure that this synchronization remains reliable, even during network disruptions, without jeopardizing channel security or creating opportunities for fraud.
Lastly, submarine swaps - atomic exchanges that bridge Lightning channels with the Bitcoin blockchain - introduce additional complexities. These operations involve intricate signature schemes that connect off-chain and on-chain transactions, creating potential attack vectors that require rigorous examination during audits.
Liquid vs Lightning: Audit Comparison
When comparing threshold key audits between Liquid and Lightning, the differences in their underlying architectures create distinct audit challenges. Liquid's federated system offers centralized and predictable audit points, while Lightning's decentralized setup requires flexible and distributed audit methods that can handle a variety of independent implementations. These architectural contrasts influence how operational, regulatory, and performance aspects are audited.
The complexity of audits varies significantly between the two networks. Liquid auditors work in a controlled environment, enabling them to apply consistent security standards across all functionaries. On the other hand, Lightning auditors must navigate a more intricate landscape, evaluating threshold key implementations across diverse node configurations, hardware setups, and software versions. Transaction processing also stands out as a key differentiator: Liquid operates with predictable block-based settlements, making retrospective analysis straightforward. In contrast, Lightning's real-time micropayments demand continuous monitoring to ensure threshold key security without disrupting network performance. Privacy considerations further separate the two, as Liquid's confidential transactions maintain clear audit trails, while Lightning's payment routing uses obfuscation techniques that make tracking threshold key usage more challenging.
Side-by-Side Audit Comparison
Here’s a breakdown of the main audit differences:
| Audit Factor | Liquid Network | Lightning Network |
|---|---|---|
| Key Management Architecture | Centralized functionary model with known entities | Decentralized model with varied key management |
| Audit Scope | Focused on functionary operations and peg-in/peg-out processes | Covers nodes, channels, and routing operations |
| Transaction Monitoring | Block-based settlement with clear finality | Real-time off-chain updates with periodic settlement |
| Security Standards | Uniform requirements across functionaries | Varies by node operator and implementation |
| Audit Frequency | Scheduled periodic reviews | Continuous monitoring for real-time operations |
| Risk Assessment | Concentrated risk in functionary compromise | Distributed risk across network participants |
| Compliance Verification | Straightforward oversight of known entities | Complex, multi-jurisdictional considerations |
| Key Recovery Procedures | Centralized disaster recovery protocols | Individual node responsibility with varied backups |
Liquid’s federated model aligns better with regulatory frameworks since auditors can collaborate directly with known functionaries who are subject to financial regulations. In contrast, Lightning’s decentralized nature complicates regulatory oversight. Individual node operators may operate under different jurisdictions or without formal regulation, making compliance verification more complex.
Audit costs also differ significantly. Liquid benefits from economies of scale, as auditors can focus on a small group of functionaries, making comprehensive reviews more cost-efficient. Lightning, however, requires distributed resources and specialized tools to monitor the entire network, driving up audit expenses and often limiting the depth of individual node evaluations.
The urgency of addressing audit findings also varies. Liquid's block-based structure allows for a more measured response, giving auditors and functionaries time to address issues before the next review. Lightning’s real-time operations, however, demand immediate responses to vulnerabilities, as exploits can occur within minutes. This requires audit systems capable of triggering automatic protections to mitigate risks quickly.
Given these differences, audit strategies must be tailored to the unique characteristics of each network. Organizations using both Liquid and Lightning need to develop specialized frameworks, employing different tools, methodologies, and expertise to ensure robust threshold key security across both systems.
sbb-itb-c977069
BitVault's Security and Compliance Features
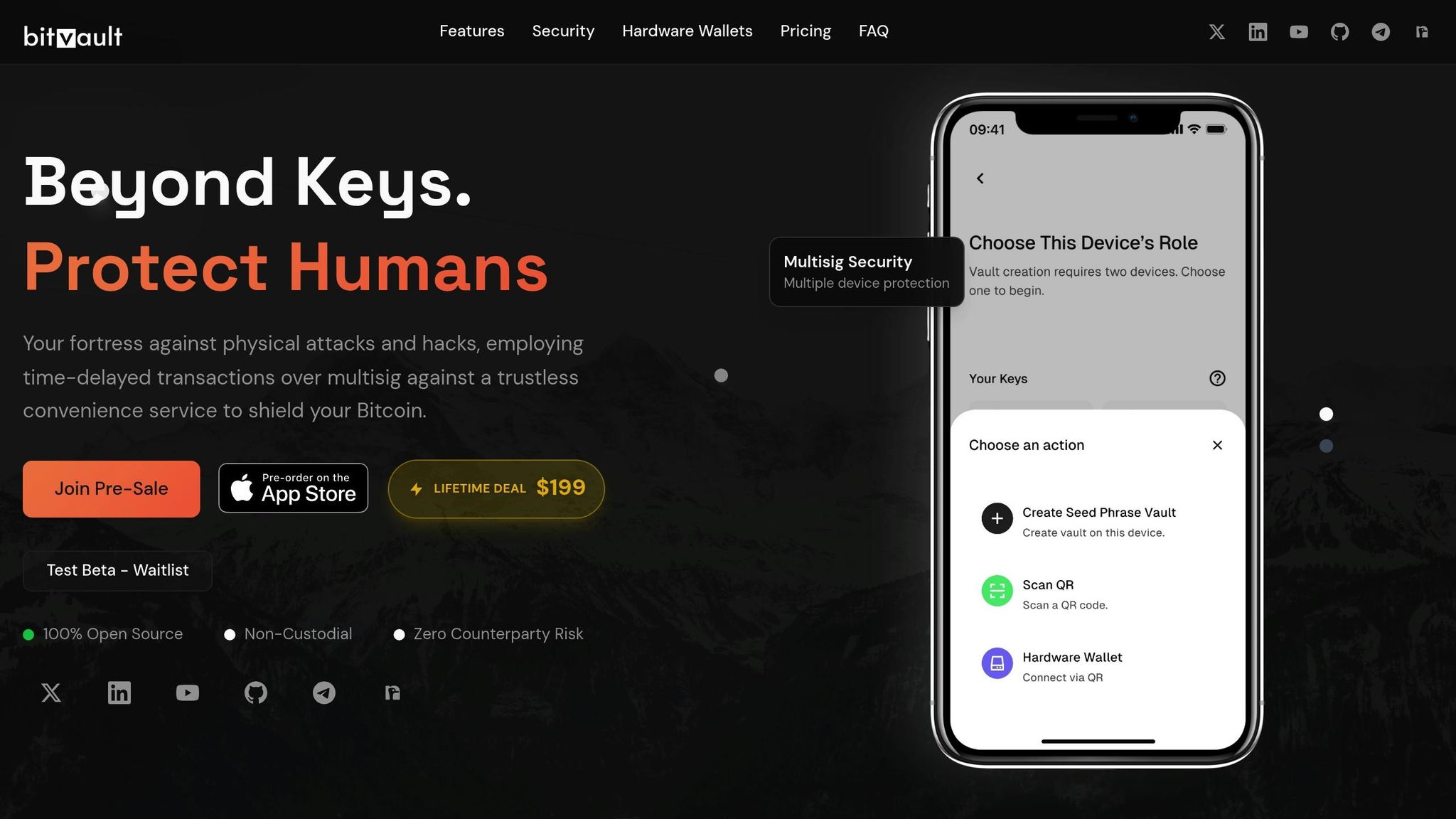
BitVault tackles the security challenges of modern networks with features designed to ensure both safety and compliance. Its open-source framework promotes transparency and allows the community to review and verify its security measures. This approach supports both the Liquid and Lightning networks with a focus on reliability and trust.
Core Security Features
At the heart of BitVault’s security is its open codebase, which fosters trust through transparency. Time-delayed transactions offer a safeguard by creating a window to verify the sequence of operations, adding an extra layer of oversight. Multisig convenience services simplify key management while boosting security, making it easier to maintain robust protocols. Additionally, real-time secret notifications provide immediate alerts when keys are accessed, enhancing the system’s responsiveness to potential threats.
Liquid and Lightning Integration
BitVault ensures smooth integration with both the Liquid and Lightning networks, maintaining consistent security practices across their distinct architectures. On the Liquid network, BitVault operates within a federated model, supporting peg-in and peg-out processes to enable seamless transfers between Bitcoin’s main chain and the Liquid sidechain. For the Lightning network, BitVault manages intricate channel states and routing details, critical for secure payment channel operations. It also optimizes L1 fees, documenting on-chain settlements to improve efficiency. These features highlight BitVault’s commitment to secure and effective network interoperability.
U.S. Security Standards Compliance
BitVault aligns with U.S. cybersecurity standards by implementing AES 256-bit encryption, a widely trusted method for safeguarding sensitive data. Its CISA+ security certification underscores its adherence to U.S. regulatory frameworks. Additionally, the platform offers customizable transaction delays, striking a balance between robust security measures and operational efficiency.
Conclusion
Threshold key audits play a crucial role in securing Bitcoin Layer 2 networks, with Liquid and Lightning requiring distinct approaches to meet their unique demands.
Liquid benefits from its structured federation, which enables predictable audits and consistent compliance. On the other hand, Lightning's dynamic channel states demand continuous oversight and adaptability. These differences present unique challenges, which BitVault is designed to address effectively.
BitVault tackles these challenges by combining open-source transparency with strong security measures, such as AES 256-bit encryption and CISA+ certification. Its features, like time-delayed transactions and multisig convenience services, add extra layers of auditable security. These capabilities align seamlessly with Liquid's federated framework and Lightning's channel-centric operations, ensuring both networks maintain high standards of security.
By supporting Liquid peg operations and Lightning channel management, BitVault bridges the gap between these Layer 2 systems, fostering consistent and reliable security practices across the board.
As Bitcoin Layer 2 networks continue to grow and adapt, the demand for audit-ready systems will only increase. Transparent and verifiable security solutions that remain efficient across different platforms are essential for the future of threshold key implementations. These strategies highlight the ongoing commitment to enhancing Bitcoin self-custody through robust and reliable key management systems.
FAQs
What are the key security challenges when auditing threshold key systems on Liquid and Lightning Networks?
Auditing Liquid and Lightning Networks comes with its own set of challenges due to the intricate nature of these systems. For Liquid, the primary focus is on safeguarding liquid staking protocols and ensuring the integrity of smart contract code. Meanwhile, audits for the Lightning Network center on addressing risks such as routing attacks, channel breaches, and weaknesses in managing off-chain transactions.
Both networks also face shared concerns, particularly around cross-chain bridge security and implementing strong key management practices. These audits play a crucial role in building trust and ensuring the secure handling of assets within these advanced Bitcoin Layer 2 solutions.
How do security audits differ between the Lightning Network's decentralized structure and Liquid's federated model?
The Lightning Network operates on a decentralized framework, which makes conducting security audits a more intricate task. Auditors must assess the integrity of a sprawling network composed of countless independent nodes and payment channels. This requires a comprehensive, system-wide evaluation to maintain trust and security throughout the entire network.
On the other hand, Liquid employs a federated model, which simplifies the auditing process. Here, the focus is on a defined group of trusted entities. Audits for Liquid primarily examine the governance and security protocols of these specific members and their interactions, making the process more streamlined compared to the distributed nature of the Lightning Network.
Although both systems prioritize security, their architectures dictate vastly different approaches to auditing and oversight.
How does BitVault enhance the security and functionality of the Liquid and Lightning Networks?
BitVault boosts the security and performance of the Liquid and Lightning Networks by working seamlessly with these Bitcoin Layer 2 solutions. It offers advanced key management and time-delayed transactions to protect user assets from both physical and digital risks, adding an extra layer of safety to every transaction.
On top of that, BitVault promotes privacy and compliance by implementing strong safeguards to prevent unauthorized access. It also equips users with tools to keep full control of their funds in a non-custodial setup. This combination ensures a secure and smooth experience for anyone using the Liquid and Lightning Networks.




