Cross-chain bridges expand Bitcoin's functionality but come with serious risks. These protocols allow Bitcoin to interact with other blockchains by locking BTC on its network and creating "wrapped" versions for use elsewhere. While this opens doors to decentralized finance (DeFi) and other opportunities, it also introduces vulnerabilities that undermine Bitcoin's core security principles.
Key risks include:
- Single points of failure: Many bridges rely on a small group of validators, making them targets for attacks.
- Smart contract flaws: Bugs in bridge code can result in stolen funds or manipulated transactions.
- Centralized control: Users give up private key control, reintroducing counterparty risk.
- Cascading failures: A compromised bridge can destabilize interconnected systems, causing widespread issues.
For maximum security, stick to native Bitcoin transactions, which avoid external dependencies. If using cross-chain bridges, minimize exposure and use tools like non-custodial wallets and multisig services to reduce risks. Solutions like BitVault offer added safeguards, but always prioritize Bitcoin's trustless design when managing assets.
2227: Anoma - How Cross-Chain Bridges Are Exposing Billions of Cryptocurrency
Cross-Chain Dependency Risks in Bitcoin
Expanding on the broader risks discussed earlier, this section dives into the specific vulnerabilities that arise from cross-chain dependencies.
Integrating cross-chain infrastructure into Bitcoin introduces risks that can undermine its native security. These dependencies open up new attack surfaces, potentially jeopardizing funds and challenging Bitcoin’s foundational security principles.
How Cross-Chain Dependencies Impact Bitcoin Transactions
Cross-chain transactions disrupt Bitcoin's traditional security model by requiring reliance on external infrastructure layers instead of solely depending on Bitcoin's well-established consensus mechanism. Each additional layer - whether it's smart contracts, validator systems, or oracles - introduces potential weak points.
One of the most pressing concerns is smart contract vulnerabilities. Cross-chain bridges rely on intricate code to handle Bitcoin locking and unlocking processes. If the smart contracts have flaws, they can be exploited, leading to unauthorized withdrawals or manipulation of assets[1][3][6].
Another critical risk is tied to validator systems. Many cross-chain bridges depend on a limited group of validators to manage private keys and approve transactions. If these validators are compromised - whether through poor key management, social engineering, or flaws in key generation tools - attackers can seize control of the bridge’s funds[1][2][4][6]. This setup creates a centralized point of failure, directly conflicting with Bitcoin’s decentralized ethos.
Oracle manipulation is another weak link. Bridges often rely on external data sources (oracles) for transaction verification across chains. If these oracles are compromised or provide inaccurate data, the integrity of the transactions can be jeopardized[2][3].
Finally, the concentration of liquidity in cross-chain bridges makes them highly appealing to attackers. These systems frequently hold substantial pools of locked assets, offering a lucrative target for hackers aiming to exploit vulnerabilities[2][4][5][6].
These risks highlight the importance of prioritizing Bitcoin's inherent security as cross-chain interactions continue to grow. Strengthening these systems is crucial to maintaining the integrity of Bitcoin's decentralized framework.
Cascading Failures and Bitcoin Security Impact
Building on the analysis of cross-chain dependency risks, this section delves into how failures in interconnected systems can snowball into larger issues. When cross-chain systems falter, the repercussions often spread rapidly, creating a domino effect that can leave Bitcoin holders vulnerable.
How Cascading Failures Work
Cascading failures in cross-chain systems function much like a chain reaction. A single malfunction in one component can ripple through interconnected systems, jeopardizing users and potentially threatening substantial Bitcoin reserves.
The tightly linked nature of cross-chain protocols amplifies this risk. For example, if a liquidity bridge is compromised, it can strain other protocols that depend on the same liquidity pools or validator networks. This stress might force some protocols to suspend operations or impose emergency measures, limiting users' access to their funds.
Shared technologies across different protocols also contribute to the rapid spread of failures. When these shared components encounter technical issues, multiple systems can be affected simultaneously, leaving Bitcoin holders unable to retrieve their funds across various platforms.
Market dynamics can make things even worse. A widely publicized bridge failure might lead to panic withdrawals, exacerbating liquidity shortages. Simultaneously, network congestion can drive up transaction fees and prolong confirmation times, making it more difficult for users to transfer their Bitcoin back to native wallets.
These cascading technical issues don’t just disrupt services - they also create opportunities for criminal exploitation.
Cross-Chain Exploits in Bitcoin Crime
The vulnerabilities exposed by cascading failures often become a playground for malicious actors. Criminals can exploit compromised cross-chain protocols to launder stolen Bitcoin or obscure transaction trails, taking advantage of the complexity and novelty of these systems.
For instance, attackers might move Bitcoin through multiple bridges, converting it into wrapped tokens across various blockchains. This process can create transaction paths that are far more challenging to trace using traditional blockchain analysis tools. Furthermore, gaps in regulatory oversight between blockchains can make these laundering methods especially appealing, as the rigorous monitoring applied to Bitcoin itself often doesn’t extend to wrapped tokens or other assets on different networks.
Automation and speed in cross-chain systems add another layer of difficulty. Stolen Bitcoin can be moved swiftly across multiple protocols, making it hard for authorities to freeze funds or follow the trail in real time. These rapid movements complicate efforts to track illicit activity and recover stolen assets.
The same features that make cross-chain systems convenient for everyday users - speed, automation, and interoperability - can also be weaponized for financial crime. As such, Bitcoin holders must carefully assess the protocols they trust to safeguard their assets.
sbb-itb-c977069
Reducing Cross-Chain Risk Exposure
When it comes to protecting Bitcoin assets, the ripple effects of cross-chain vulnerabilities demand proactive strategies. The goal? Minimize exposure to risky cross-chain infrastructure while still making the most of Bitcoin's growing ecosystem. Let’s explore some practical steps to reduce these risks and how BitVault puts them into action.
Best Practices for Bitcoin Security
To keep Bitcoin secure, start with non-custodial wallets. These wallets let you maintain full control over your assets, cutting out risky third-party involvement. Here are some key strategies to consider:
- Time-delayed transactions: These give you a crucial window to review and cancel suspicious transfers before they’re finalized.
- Multisig services: By requiring multiple keys to authorize a transaction, these add an extra layer of security - even if one key is compromised.
- Open-source wallets: Wallets with publicly available code allow independent experts to audit for vulnerabilities, ensuring they stay resilient against potential threats.
Each of these measures directly counters the risks that come with relying on cross-chain systems, providing a stronger foundation for Bitcoin security.
How BitVault Protects Against Cross-Chain Risks
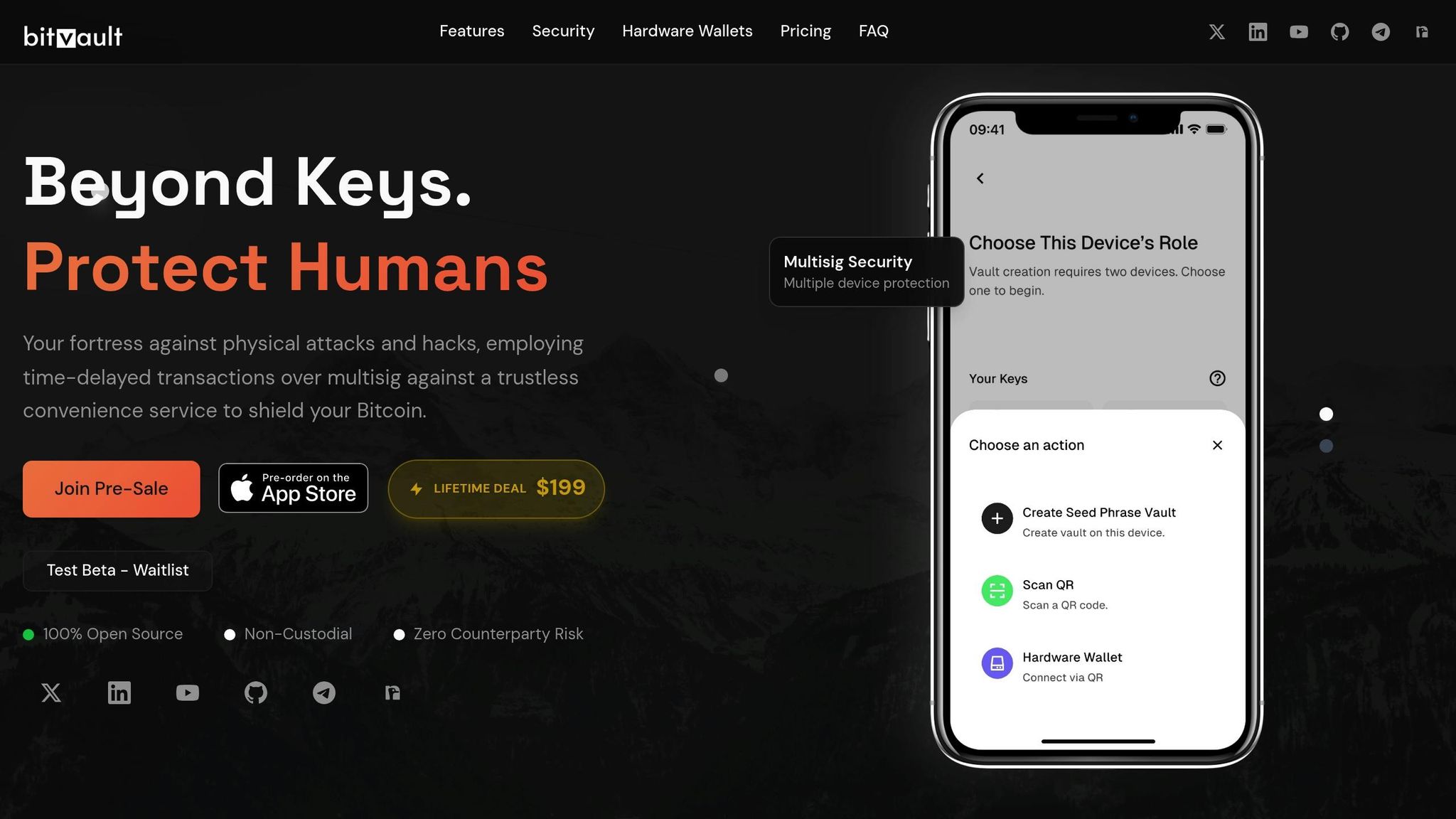
BitVault takes a hands-on approach to tackle cross-chain vulnerabilities. Its design prioritizes decentralization and user control, addressing the risks that centralized systems often introduce. Here’s how BitVault stands out:
- Non-custodial design: By keeping private keys in the hands of users, BitVault reduces reliance on third parties and eliminates single points of failure.
- Open-source transparency: BitVault’s code is open for public review, ensuring vulnerabilities can be identified and addressed by the wider Bitcoin community.
- Integration with Bitcoin Layer 2 solutions: Native support for technologies like the Liquid Network and Lightning Network allows users to access Bitcoin’s ecosystem securely, without the usual cross-chain complications.
- Built-in safeguards: Features like time-delayed transactions and multisig controls are part of BitVault’s core design, offering robust protection without needing external dependencies.
Risk Comparison: Cross-Chain Bridges vs Native Bitcoin Transactions
When evaluating the risks associated with Bitcoin transactions, it's essential to consider the trade-offs between cross-chain bridges and native Bitcoin transactions. Each option serves different purposes and comes with its own set of challenges and advantages.
Cross-chain bridges enable Bitcoin to interact with other blockchains, offering greater functionality and flexibility. However, this added capability comes with increased complexity and potential vulnerabilities. These bridges rely on external protocols, such as smart contracts or validator networks, which can introduce additional risks.
On the other hand, native Bitcoin transactions remain entirely within Bitcoin's ecosystem. They rely on the network's well-established Proof-of-Work consensus mechanism, avoiding external dependencies and maintaining a simpler, more secure framework.
In short, cross-chain bridges are ideal for users seeking interoperability across blockchains, while native Bitcoin transactions are the go-to choice for those prioritizing security above all else.
Risk and Benefit Comparison Table
| Factor | Cross-Chain Bridges | Native Bitcoin Transactions |
|---|---|---|
| Security Model | Relies on smart contracts and validator networks, introducing potential attack risks | Secured by Bitcoin's Proof-of-Work consensus, free from external dependencies |
| Complexity | Involves multiple technical components, increasing overall system complexity | Operates solely within Bitcoin's ecosystem, keeping the process straightforward |
| Functionality | Enables cross-chain connectivity and access to other blockchain networks | Focuses on Bitcoin's core capabilities, prioritizing reliability and security |
This breakdown illustrates why native transactions are often preferred for high-security needs, while cross-chain bridges are used selectively for accessing extended blockchain features.
Conclusion: Securing Bitcoin in a Cross-Chain World
As blockchain networks become more interconnected, new opportunities emerge for Bitcoin holders. However, with these opportunities come serious security challenges that demand careful attention. Cross-chain bridges, while enabling access to decentralized finance protocols and added functionality, compromise Bitcoin's core security by introducing external dependencies.
Native Bitcoin transactions remain the gold standard for security. Backed by Bitcoin's Proof-of-Work consensus mechanism, which has operated reliably for over 15 years without major breaches, they offer unmatched protection. In contrast, using cross-chain bridges sacrifices this proven security for the sake of convenience and expanded functionality.
Despite the risks, cross-chain solutions continue to attract users due to their capabilities. The best strategy is to limit exposure and prioritize protection. This involves thoroughly researching any bridge protocol, understanding its risks, and only committing Bitcoin you can afford to lose when engaging in cross-chain activities.
Given these risks, implementing robust security measures is non-negotiable. Tools like BitVault tackle many vulnerabilities tied to cross-chain interactions. Its time-delayed transactions act as a safeguard against technical failures and social engineering attacks. Multisig services add extra layers of protection, while the secret notification system alerts users to unauthorized transaction attempts, potentially preventing significant losses.
As the blockchain ecosystem evolves, Bitcoin holders must carefully weigh the trade-offs between functionality and security. While innovation is crucial, it should not come at the expense of Bitcoin's proven safety. Cross-chain bridges, by their nature, introduce complexities that native Bitcoin transactions avoid.
The path forward lies in adopting solutions that uphold Bitcoin's core security principles while enabling safe participation in the broader blockchain landscape. A balanced approach - embracing thoughtful innovation alongside tools like BitVault - empowers Bitcoin holders to explore cross-chain opportunities without compromising the security that defines Bitcoin's value.
FAQs
What security risks do cross-chain bridges pose to Bitcoin transactions?
Cross-chain bridges come with a host of security challenges for Bitcoin transactions, largely stemming from their complexity and dependence on external systems. For instance, vulnerabilities in smart contract code can be exploited by attackers, leading to potential breaches. Similarly, centralization risks - where a single point of failure exists - pose a significant threat to the stability and security of the entire bridge.
Other concerns include liquidity issues and oracle manipulation, both of which can open the door to asset theft or tampering. On top of that, poor private key management and the intricate nature of these systems amplify the chances of security failures, which could result in substantial financial losses and undermine Bitcoin's broader security framework.
To reduce these risks, users should thoroughly assess the security protocols of any cross-chain solution they plan to use. Opting for tools like non-custodial wallets, which emphasize strong security measures, can provide an added layer of protection against these vulnerabilities.
What steps can Bitcoin holders take to reduce risks when using cross-chain systems?
To minimize risks when using cross-chain systems, Bitcoin holders should prioritize security and follow smart practices. Start by choosing trusted bridges that have been through multiple security audits and adhere to widely accepted protocols. This can help ensure more reliable interactions between networks.
Keep your assets in bridge protocols for as short a time as possible, and avoid transferring large sums in one go. It's also crucial to confirm that any smart contracts involved have been rigorously audited to rule out vulnerabilities. Opting for secure cross-chain messaging systems with features like immutability and thorough security checks can add an extra layer of protection for your funds.
For enhanced safety, explore wallets like BitVault. These wallets come with advanced security features and support for Bitcoin Layer 2 solutions, providing both strong protection and smooth interoperability.
Why are Bitcoin's native transactions safer than cross-chain activities?
Bitcoin transactions are considered safer because they occur directly on the Bitcoin blockchain. This eliminates the need for third-party bridges or external protocols, which are often a weak point and can be exploited by hackers.
By using native Bitcoin transactions, you avoid the risks tied to these external systems, offering a more secure and dependable way to handle your Bitcoin assets.




